Looking at the top left in Google Chrome, you may see a red X–Google’s way to denote unsecured SSL (Secure Sockets Layer). Non-HTTPS sites also face consequences of the 2016 update to Google’s security measures, potentially confusing WordPress users and other login pages that appear to have been compromised (while this is just Google’s way of denoting a non-HTTPS site).
Also, as consumer electronics manufacturers release new and more complex gadgets, security is likely to be the last thing on people’s minds. Devices like Apple’s HomeKit turn your iPhone or iPad into a remote control for lights, locks, the thermostat, window shades and even your doorbell, making typical iOS functions like Siri voice-based extensions of controlling a smart home.
Yet even if most electronics on a home network employ top security standards, all it takes is a faulty webcam for an attack to happen.
We just saw this with internet infrastructure company Dyn in late October of 2016. Mirai malware took advantage of default, easy-to-guess passwords on the webcams of unsuspecting consumers, leading to a massive Distributed Denial of Service (DDoS) attack temporarily shutting down popular sites like Twitter and PayPal.
Along with Apple’s Authentication Coprocessor, HomeKit’s end-to-end encryption helps mitigate the risk of hacking. The coprocessor only sends a certificate that allows an iOS device to unlock an accessory (like your home’s light dimmers, thermostat and power meter) after the accessory completes a challenge sent by the iOS device. Any Internet of Things device that connects to this network, however, may not have the same robustness rules in place.
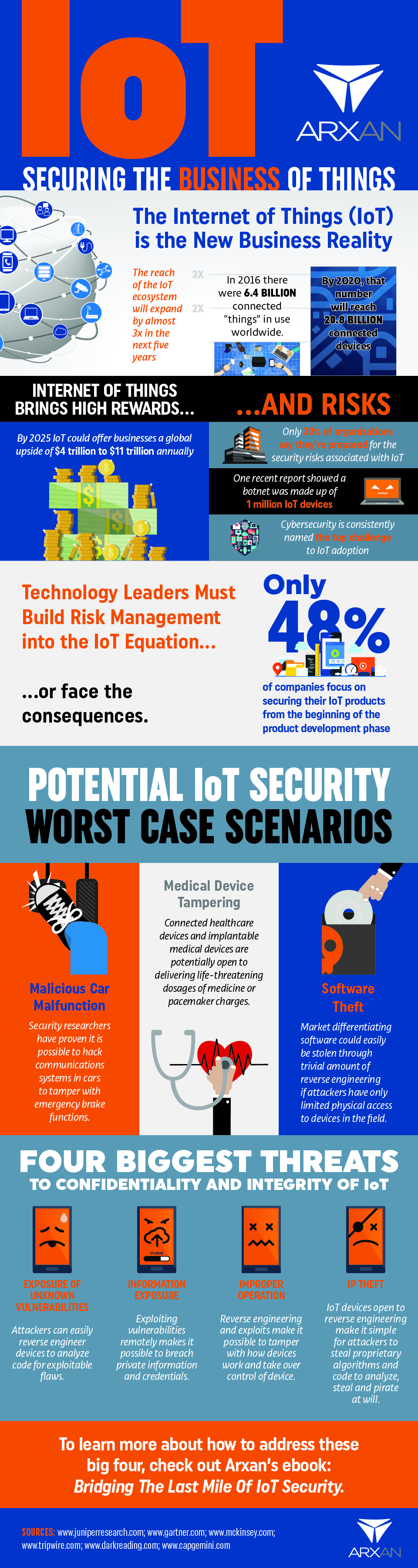
According to this graphic from Arxan, the number of devices connected to the internet reached 6.4 billion in 2016. According to cisco, the estimate number of connected devices is expected to grow to 50 billion by 2020! Thus, in-home communication network security is only half the battle for consumers, as the cars they drive are increasingly becoming connected as well. Car manufacturers have different OEMs when it comes to displays and in-vehicle digital storage, meaning that all devices in a connected car may not use end-to-end encryption. Code scanners can interrupt critical functions and if you look further into automotive IoT security you’ll find that many parts of a vehicle that have been around for years–like the OBD2 port for engine diagnostics and on-board computers–could potentially be decrypted and injected with malware.
On the issue of DDoS attacks, Arxan CMO Mandeep Khera explains that “hackers go after the weakest attack vectors and it’s increasingly apparent that IoT infrastructure from devices and sensors to the embedded software to APIs is the weakest link.”
The idea of a smart home we see today has been around since the early 2000s, when structured wiring came into focus as a way to connect video and networking devices to DSL, which offered higher speed internet access than over a phone line. Fast forward to wireless technology in 2016, and connected homes are easier to set up, but vulnerable in different ways.
A lot of today’s IoT hardware, including the consumer webcams that were hacked during the DDoS attack targeting Dyn’s infrastructure, can still access Telnet after changing the default username and password of the system. This keeps the door open for remote hacking and without wireless chip security standards you find in HomeKit, it can be more difficult to build a secure network of non-iOS devices.
Cisco neatly outlines the security challenges within IoT systems including Management of multi-party networks, crypto resilience, physical protection and more in this article.
This detailed article by IBM highlights things you can do to secure your IoT devices with mechanisms such as User ID authentication, One Time Passwords, server unique ID authentication and more and offers comprehensive ways to implement such mechanisms.
Contributors:
-
Graphic and content contributor: Arxan Technologies
-
Arxan is an application attack-prevention and self-protection firm with products for Internet of Things (IoT), Mobile, Desktop, and other applications. The company’s headquarters and engineering operations are based in the United States with global offices in EMEA and APAC.
-
Quote contributor: Mandeep Khera, Arxan CMO
-
Mandeep Khera, who gave a quote for this article, is responsible for all marketing and business development functions globally for Arxan. Mandeep brings over two decades of experience in Software/SaaS/Managed Services Marketing in the areas of application security, IoT, Big Data and other enterprise software applications to Arxan.
There is no ads to display, Please add some