What is “WannaCry’?
WannaCry is a ransomware attack that has (in)famously brought much of the world’s computers and servers to a complete standstill including critical systems such as UK’s healthcare network, Russia’s government systems and those of the Indian state, Andhra Pradesh. It makes use of an SMB (Server Message Block) vulnerability on Windows systems and spread rapidly across networks.
How does it work and where did it originate?
Many experts suspect that WannaCry aka WannaCrypt was based on some exploits leaked from the US Government’s NSA toolkit for cyber-attacks and works by encrypting all files in a server/device and threatening to delete all files unless a ransom of $300 is paid in the form of BitCoins. The attack is allegedly being orchestrated by a group that calls itself ShadowBrokers.
How do I know which systems are affected?
Most servers and personal computers that operate Windows 8 or older versions and do not have the latest security patches/updates from Microsoft are likely to be vulnerable. In this post, we address the steps you should take to protect your Windows Dedicated Server purchased from ResellerClub.
What do you need to do to protect your ResellerClub Windows Dedicated Server from a WannaCry?
Below are the steps you need to take to update/patch your Windows OS. Besides following the below steps, we strongly suggest that you install all latest patches released by Microsoft as there are newer, more resistant versions of the ransomware being reported in some countries.
You can update Windows using GUI and CUI. Although both the methods help you in doing some recommend that you should use GUI as there are very little chances of an error and it is easy to troubleshoot in case of issues.
Using GUI
Below are the steps you need to take in order to update/patch your windows using graphical user interface.
Step 1: Open the Windows update control panel. To open the same go, to Start > Type “windows update” > Enter or Start > Run > Type “wuapp.exe” in the run window and press enter.
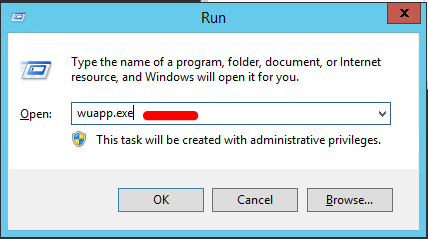
Step 2:
A. Click on “Check online for updates from Windows Update”. or
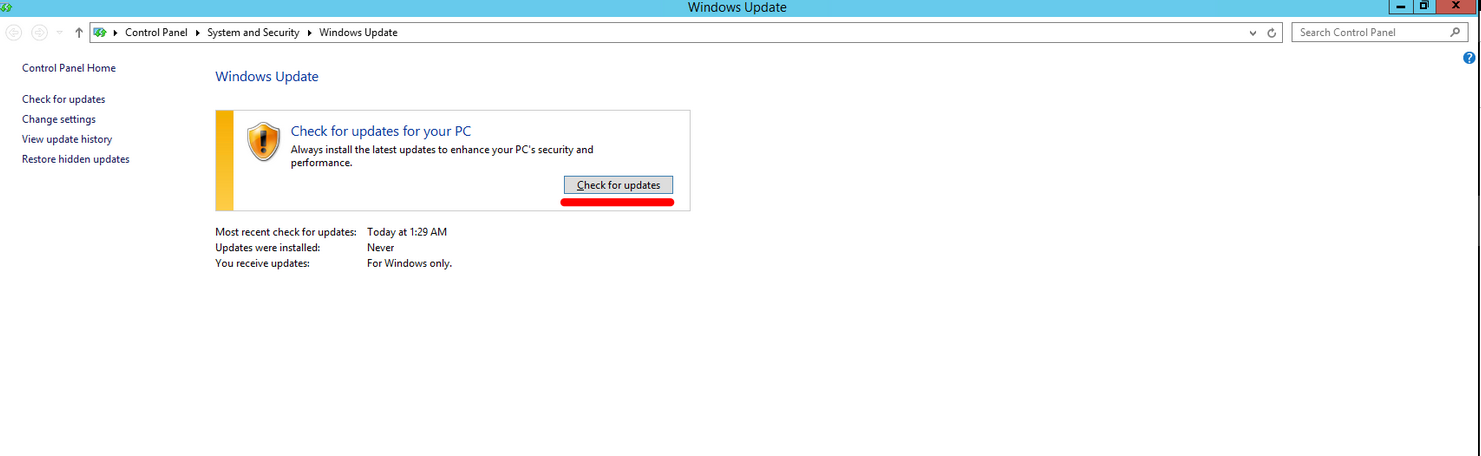
B. “Check for updates” whichever is available from A and B
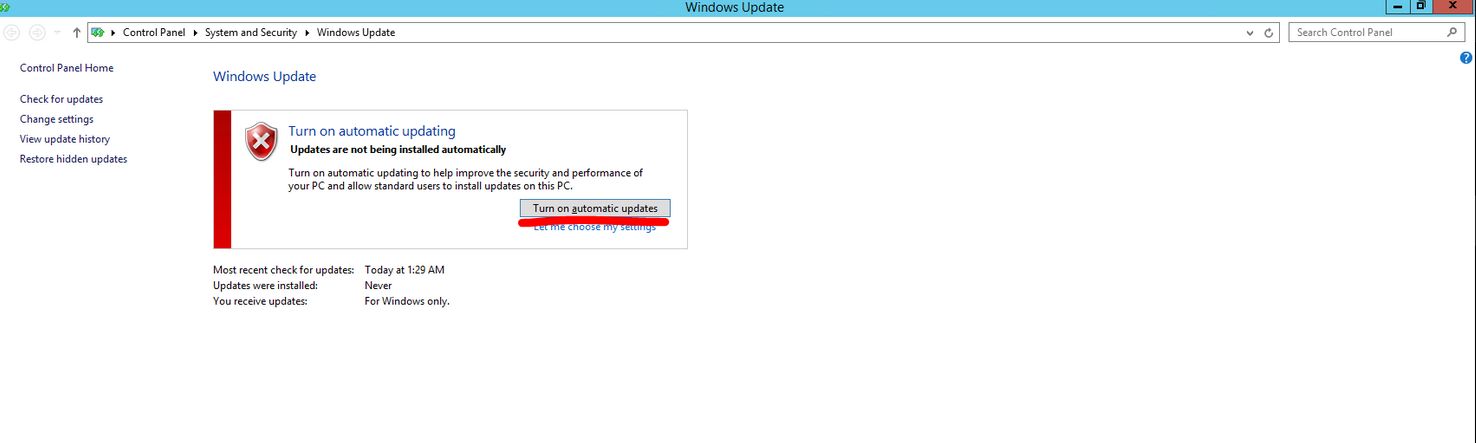
C. If the automatic updating is not enabled in windows update setting then it will give an error, if it is the case then click on “Turn on automatic updates”
A
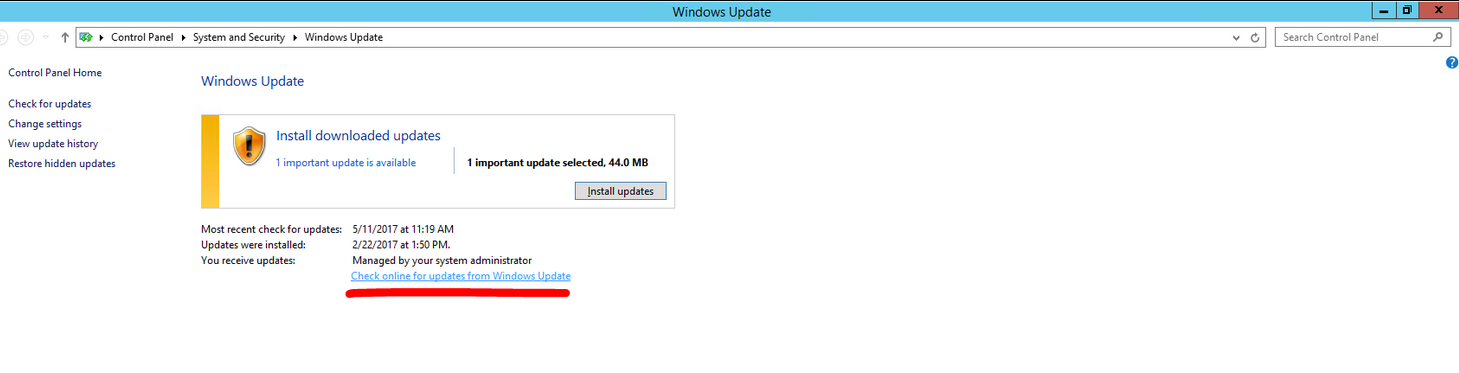
B
C
Step 3: Select all important updates and click on “Install Updates”.
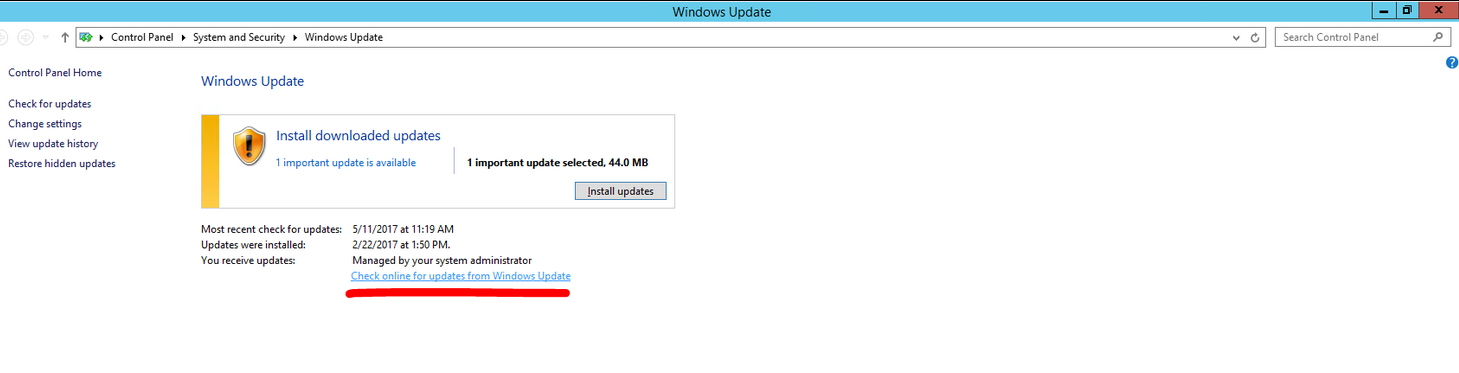
Step 4: As soon as the installation is finished, click on “Restart now” to reboot the server.
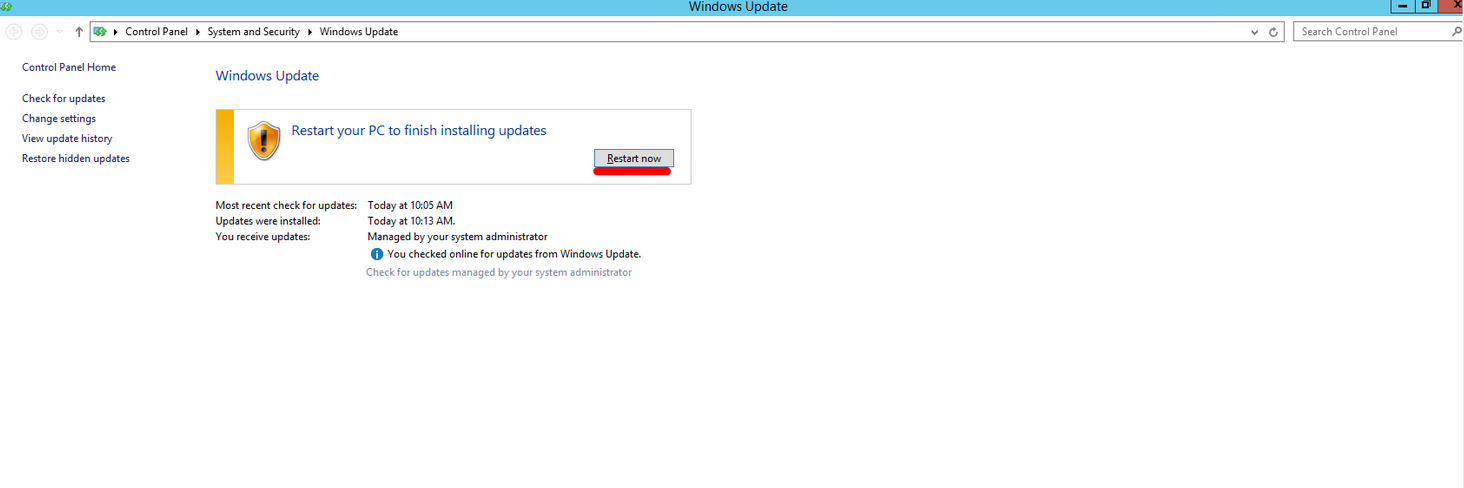
Step 5: After the reboot, start over with step 1 to ensure that there are no pending updates.
Using CUI
Below are the steps you need to take in order to update/patch your windows using Command line interface.
Method 1: Using Native Commands

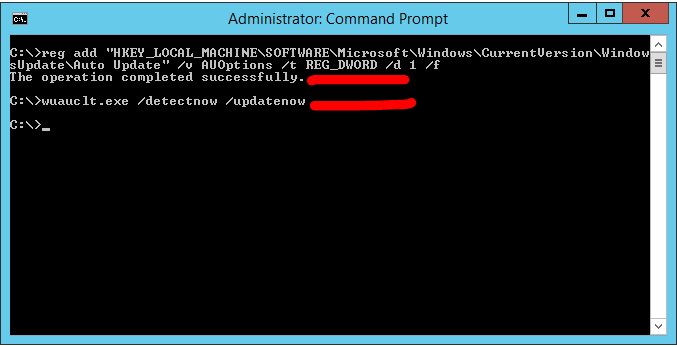
Step 2: To check and update Windows, type the below command and press enter.
Command:
- reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update” /v AUOptions /t REG_DWORD /d 1 /f
- wuauclt.exe /detectnow /updatenow
Note: This will not work if you have set “Never check for updates” in Windows Update settings. In this case go for GUI option given above.
Step 3: After running the same when you open the Windows update control panel, you will be able to see the status of the installation.
Note: You will be able to see the status after at least 5-10 minutes of running the command as it will detect the updates first then it will start preparing to install the updates. If the status is not being shown then it is better to go for GUI option. Although you can check the status in the following log if you want to troubleshoot: C:\Windows\WindowsUpdate.log
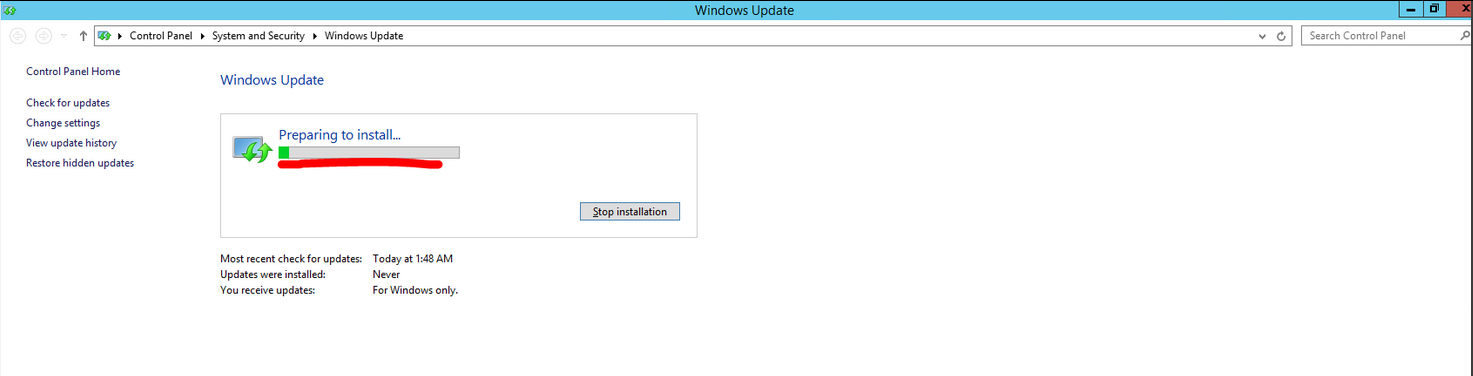
Step 4: Once the installation is finished, reboot the server by clicking on “Restart now”
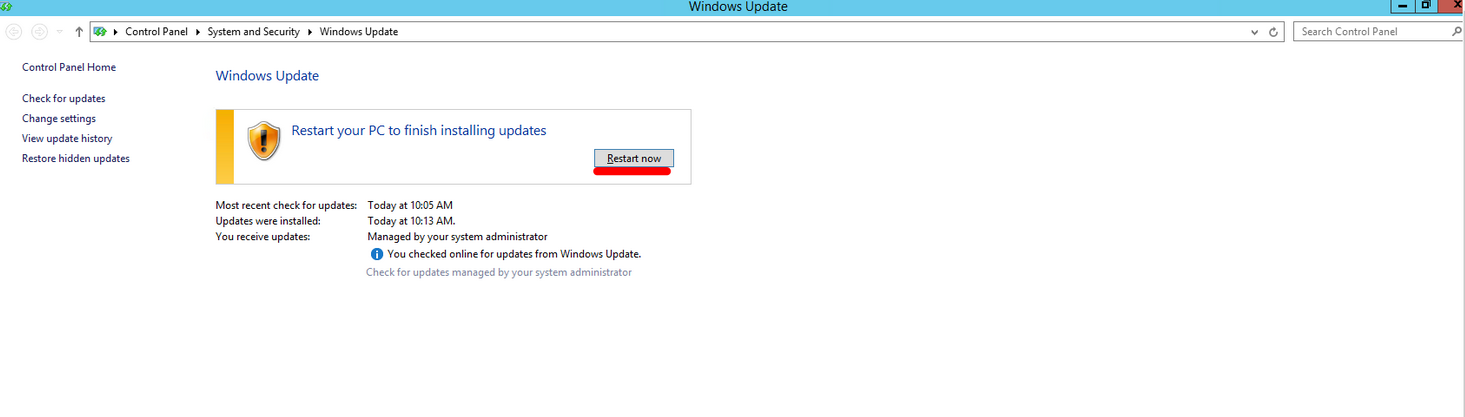
Step 5: After the reboot, start over with the step 1 to ensure that there are no pending updates.
Method 2: Using VB Script
To update Windows using a VB script provided by Microsoft in the below link, you have to follow the instructions provided in the link itself.
Note: We have tested the same on our test server and the script works seamlessly. You might have to enable automatic updating using below command before running the script
reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update” /v AUOptions /t REG_DWORD /d 1 /f
https://msdn.microsoft.com/en-us/library/aa387102(v=vs.85).aspx
Verification Steps For SMB Attack Vulnerability After The Update
Verify on Windows 2008 R2
There are two patches released by Microsoft for Windows 2008 R2 as per the following document.
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
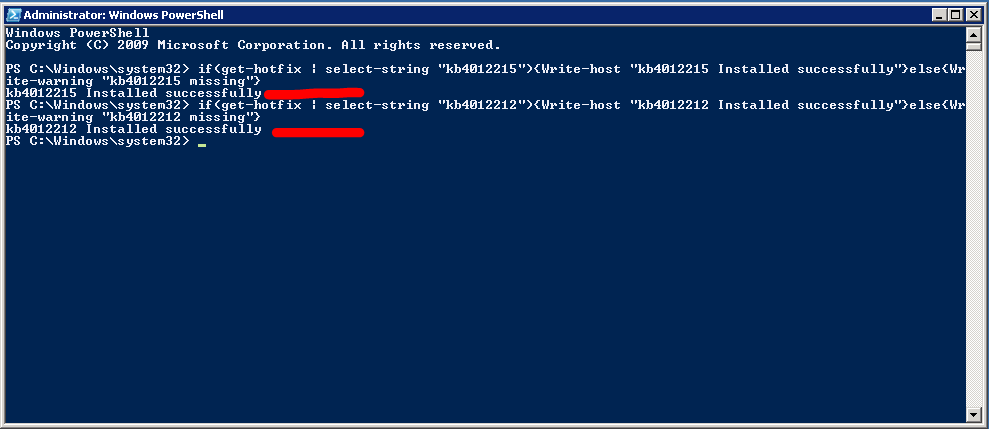
- KB4012215
- KB4012212
Open Powershell window as Administrator and run below command:
if(get-hotfix | select-string “kb4012215”){Write-host “kb4012215 Installed successfully”}else{Write-warning “kb4012215 missing”}
if(get-hotfix | select-string “kb4012212”){Write-host “kb4012212 Installed successfully”}else{Write-warning “kb4012212 missing”}
The output will tell you if the server is patched properly, or if the update is missing.
Verify on Windows 2012 R2
There are two patches released by Microsoft for Windows 2012 R2 as per the following doc.
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
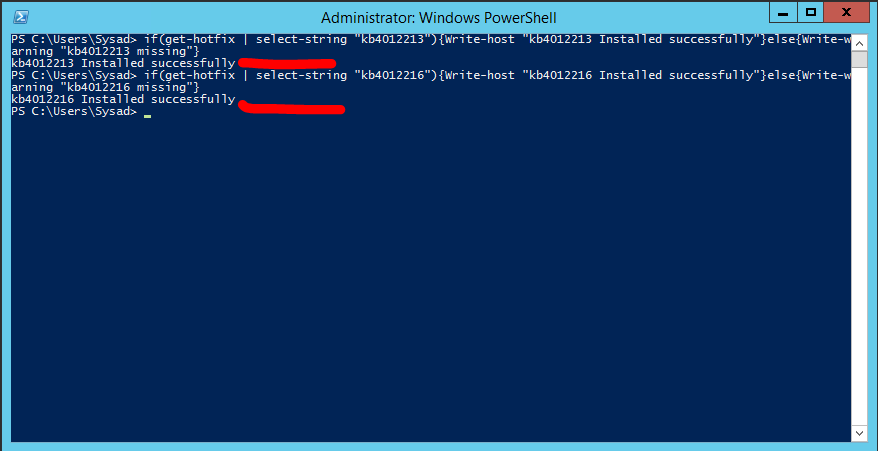
- KB4012213
- KB4012216
Open Powershell window as Administrator and run below command:
if(get-hotfix | select-string “kb4012213”){Write-host “kb4012213 Installed successfully”}else{Write-warning “kb4012213 missing”}
if(get-hotfix | select-string “kb4012216”){Write-host “kb4012216 Installed successfully”}else{Write-warning “kb4012216 missing”}
The output will tell you if the server is patched properly or the update is missing.
Follow these simple steps to install Microsoft’s security patch to tackle the situation. It’s best that you have this done as soon as possible to protect yourself.
References
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
https://msdn.microsoft.com/en-us/library/aa387102(v=vs.85).aspx
There is no ads to display, Please add some



